Android malware Crocodilus adds fake contacts to spoof trusted callers

The latest version of the 'Crocodilus' Android malware has introduced a new mechanism that adds a fake contact to an infected device's contact list to deceive victims when they receive calls from the threat actors.
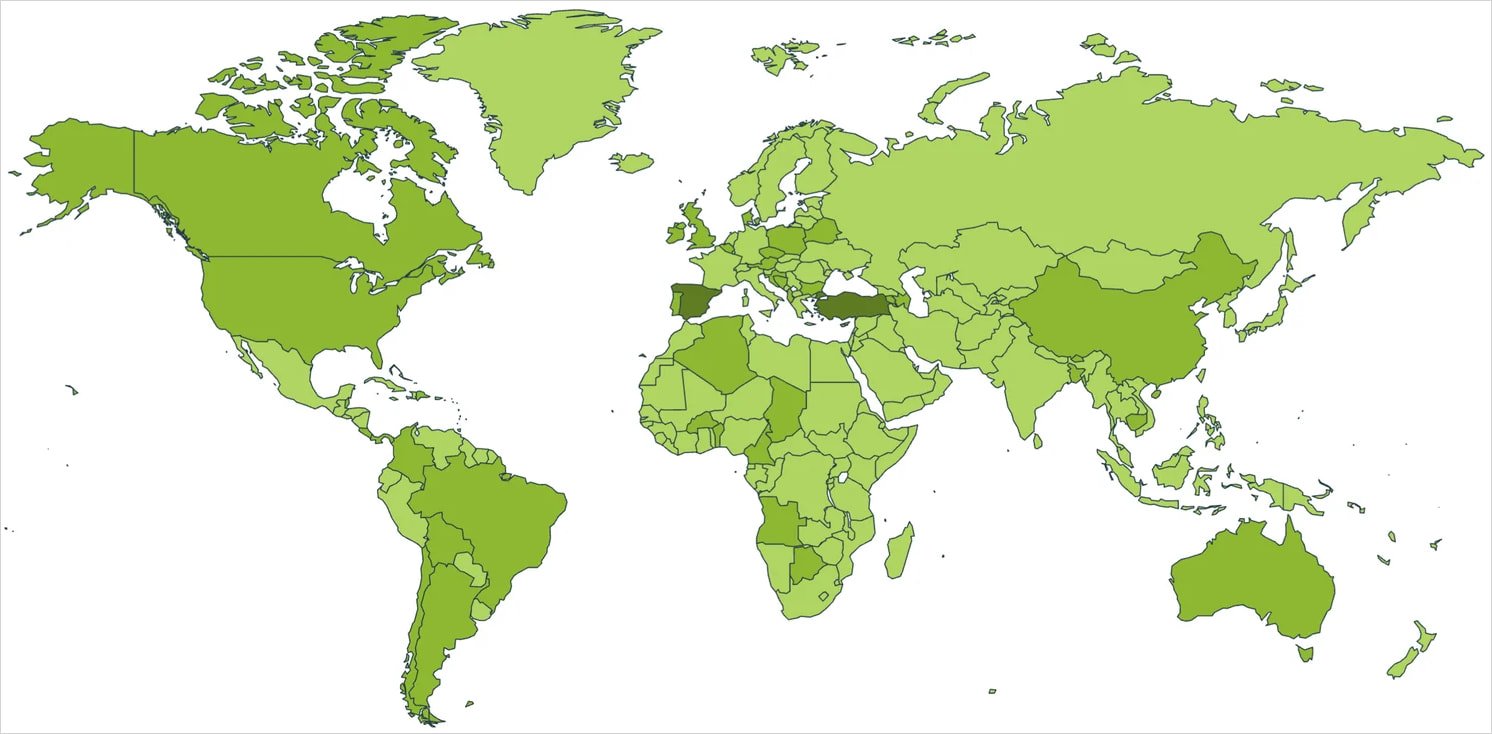
This feature was introduced along with several others, mostly evasion-focused improvements, as the malware appears to have expanded its targeting scope worldwide.
Crocodilus goes global
The malware was first documented by Threat Fabric researchers in late March 2025, who highlighted its extensive data-theft and remote control capabilities.
Those early versions also featured elementary attempts at social engineering via bogus error messages requesting the user's cryptocurrency wallet key to be "backed up" within 12 hours or lose access to it.
At the time, Crocodilus was only seen in a few small-scale campaigns in Turkey.
This has now changed, according to Threat Fabric, which continued monitoring the malware operation and observed that Crocodilus has expanded its targeting scope to all continents.
At the same time, the latest releases introduced improved evasion through code packing on the dropper component and an extra layer of XOR encryption for the payload.
The analysts have also seen code convolution and entanglement that makes reverse engineering the malware more difficult.
Another addition is a system to parse stolen data locally on the infected device before exfiltrating it to the threat actor for higher-quality data collection.
Fake contacts
A notable feature in the latest Crocodilus malware version is the ability to add fake contacts on the victim's device. Doing so would cause the device to display the name listed in a caller's contact profile rather than the caller ID when receiving an incoming call.
This could allow the threat actors to impersonate trusted banks, companies, or even friends and family members, making the calls appear more trustworthy.
This action is performed upon issuing a specific command that triggers the following code to programmatically (using ContentProvider API) create a new local contact on the Android device.
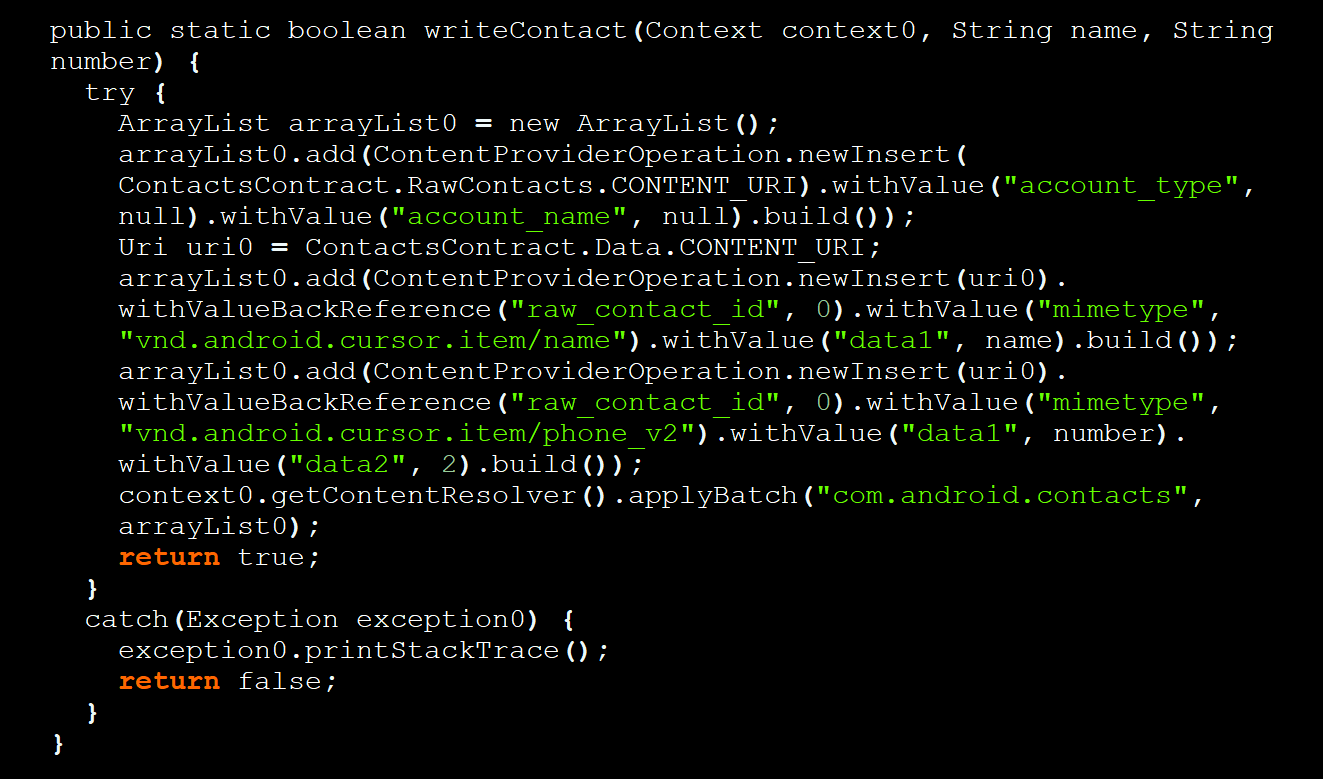
"Upon receiving the command "TRU9MMRHBCRO", Crocodilus adds a specified contact to the victim's contact list," explains Threat Fabric in the report.
"This further increases the attacker's control over the device. We believe the intent is to add a phone number under a convincing name such as "Bank Support," allowing the attacker to call the victim while appearing legitimate."
The rogue contact is not tied to the user's Google account, so it won't sync with other devices where they're logged in.
Crocodilus is evolving quickly, demonstrating an affinity to social engineering, which makes it a particularly dangerous malware.
Android users are advised to stick to Google Play or trusted publishers when downloading software for their devices, ensuring that Play Protect is always active and minimizing the number of apps they use to the absolute necessary.
Google patches new Chrome zero-day bug exploited in attacks
Android Trojan Crocodilus Now Active in 8 Countries, Targeting Banks and Crypto Wallets
Free online web security scanner