BidenCash carding market domains seized in international operation

Earlier today, law enforcement seized multiple domains of BidenCash, the infamous dark web market for stolen credit cards, personal information, and SSH access.
The illegal shop’s domain on the dark web now redirects to the Secret Service’s domain for seizing websites involved in illegal activities.
An official banner informs visitors that the BidenCash domain has been seized by U.S. law enforcement as part of an international operation led by the United States Secret Service (USSS) and the Federal Bureau of Investigation.
The two U.S. agencies were supported in the operation by the Dutch National Police (Politie), the nonprofit security organization The ShadowServer Foundation, and the real-time attack surface visibility company Searchlight Cyber.

According to security researcher g0njxa, the clear web domain on the .asia TLD for the carder marketplace also redirects to the Secret Service's usssdomainseizure.com domain. Some domains are still online, according to some reports.
A press release from the Department of Justice informs that the operation seized about 145 domains and cryptocurrency associated with the BidenCash marketplace both on the clearweb and on the darknet.
"BidenCash administrators charged a fee for every transaction conducted on the website," which generated more than $17 million in revenue since it emerged in 2022.
According to the DoJ, the illegal market had more than 117,000 customers and helped traffick over 15 million payment card numbers along with personally identifiable information belonging to card owners.
BidenCash's card data leaks
Illegal card shops have been around for more than two decades. Initially, card data was typically collected in large amounts from PoS malware, which harvested the temporarily unencrypted card data from the memory of a point-of-sale (PoS) terminal.
More recently card information was stolen using web skimmers - malware planted on online shops to collect payment details from customers at checkout.
BidenCash started in March 2022 to fill the void left by the shutdown of Joker’s Stash card market about a year earlier and the Russian authorities seizing multiple card shops that included Forum, Trump Dumps, and UniCC.
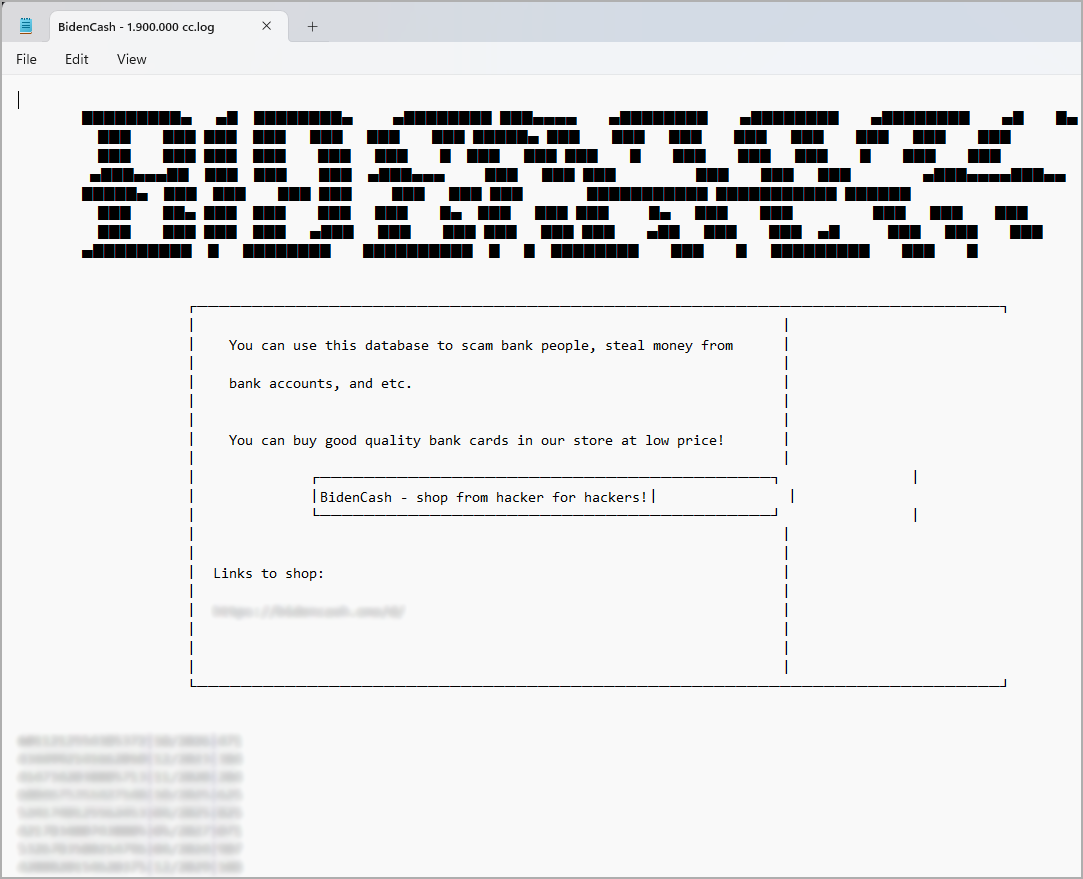
Since the beginning, the administrators of BidenCash tried to attract attention, not just through the name of the card shop but also by leaking large amounts of card information.
They started with a small leak in June 2022 of a database with just 6,600 credit cards but included millions of email addresses.
A few months later, in October, BidenCash leaked a set of 1.2 million credit cards in an effort to promote their services.
Most of the cards were from users in the U.S., expiration dates varied between 2023 and 2026, and covered a wide geography.
In 2023, the marketplace leaked two additional databases [1, 2] that cumulatively counted more than 4 million credit cards.
Although administrators of such services often try to restore their operations, these seizures have a significant impact on illegal activities.
The U.S. Secret Service is actively involved in fighting financial fraud that involves credit cards, money laundering, cryptocurrency scams, or identity theft operations.
At the end of May, the agency and multiple state and local law enforcement partners visited more than 411 businesses in search of illegal skimming devices at ATMs, gas pumps, and point-of-sale (PoS) terminals.
While just 17 skimmers were recovered, it is estimated that the action prevented a potential loss of more than $5 million.
Update [June 4th, 14:19]: Article updated with information the U.S. Department of Justice published in a press release.
Ukraine claims it hacked Tupolev, Russia’s strategic warplane maker
FBI warns of NFT airdrop scams targeting Hedera Hashgraph wallets
Free online web security scanner