CISA Warns of Active Exploitation of Linux Kernel Privilege Escalation Vulnerability

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Tuesday placed a security flaw impacting the Linux kernel in its Known Exploited Vulnerabilities (KEV) catalog, stating it has been actively exploited in the wild.
The vulnerability, CVE-2023-0386 (CVSS score: 7.8), is an improper ownership bug in the Linux kernel that could be exploited to escalate privileges on susceptible systems. It was patched in early 2023.
"Linux kernel contains an improper ownership management vulnerability, where unauthorized access to the execution of the setuid file with capabilities was found in the Linux kernel's OverlayFS subsystem in how a user copies a capable file from a nosuid mount into another mount," the agency said.
"This uid mapping bug allows a local user to escalate their privileges on the system."
It's currently not known how the security flaw is being exploited in the wild. In a report published in May 2023, Datadog said the vulnerability is trivial to exploit and that it works by tricking the kernel into creating a SUID binary owned by root in a folder like "/tmp" and executing it.
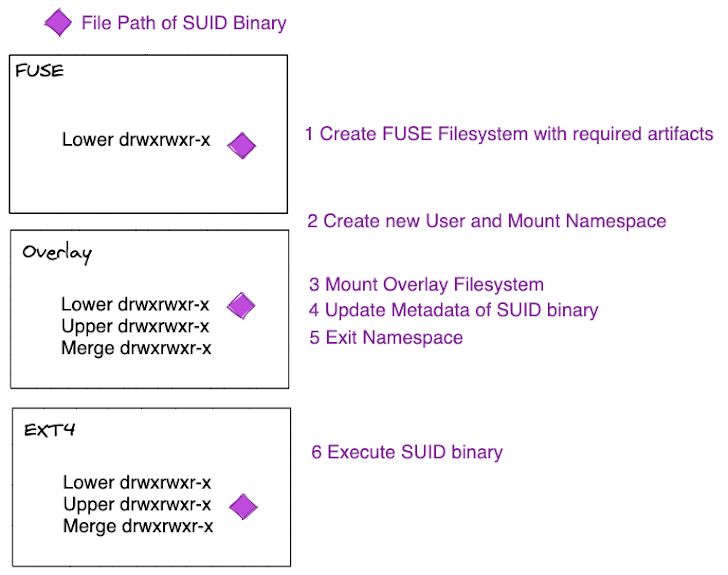
"CVE-2023-0386 lies in the fact that when the kernel copied a file from the overlay file system to the 'upper' directory, it did not check if the user/group owning this file was mapped in the current user namespace," the company said.
"This allows an unprivileged user to smuggle an SUID binary from a 'lower' directory to the 'upper' directory, by using OverlayFS as an intermediary."
Later that year, cloud security firm Wiz detailed two security vulnerabilities dubbed GameOver(lay) (CVE-2023-32629 and CVE-2023-2640) affecting Unix systems that led to similar consequences as CVE-2023-0386.
"These flaws allow the creation of specialized executables, which, upon execution, grant the ability to escalate privileges to root on the affected machine," Wiz researchers said.
Federal Civilian Executive Branch (FCEB) agencies are required to apply the necessary patches by July 8, 2025, to secure their networks against active threats.
Asana warns MCP AI feature exposed customer data to other orgs
Ex-CIA Analyst Sentenced to 37 Months for Leaking Top Secret National Defense Documents
Free online web security scanner