Stolen Ticketmaster data from Snowflake attacks briefly for sale again

The Arkana Security extortion gang briefly listed over the weekend what appeared to be newly stolen Ticketmaster data but is instead the data stolen during the 2024 Snowflake data theft attacks.
The extortion group posted screenshots of the allegedly stolen data, advertising over 569 GB of Ticketmaster data for sale, causing speculation that this was a new breach.
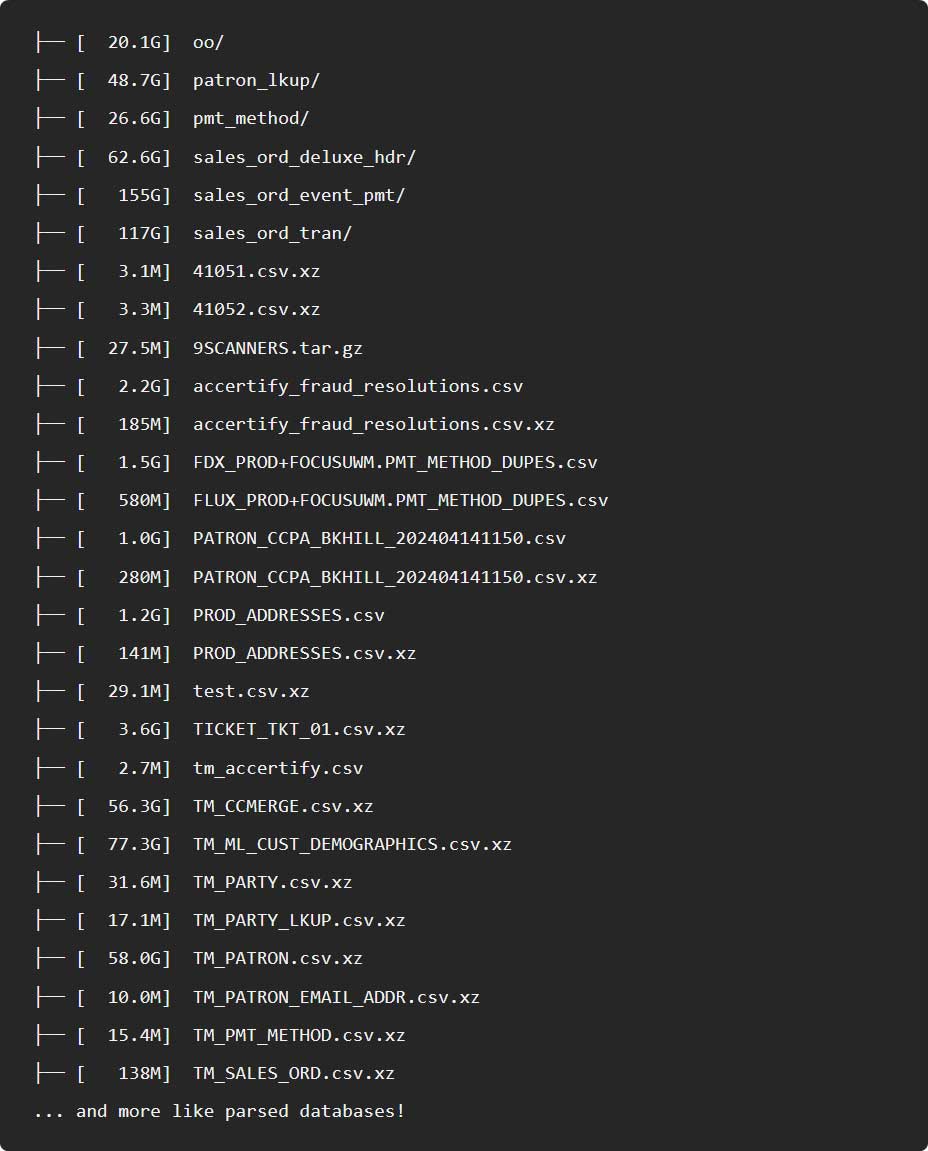
However, BleepingComputer has determined that the files shown in the Arkana post match samples of Ticketmaster data we previously saw during the 2024 Snowflake data theft attacks.
Furthermore, one of the images had the caption "rapeflaked copy 4 quick sale 1 buyer," which is a reference to a tool named "RapeFlake."
RapeFlake is a custom tool created by the threat actors to perform reconnaissance and exfiltrate data from Snowflake's databases.
As previously reported, the Snowflake attacks targeted many organizations, including Santander, Ticketmaster, AT&T, Advance Auto Parts, Neiman Marcus, Los Angeles Unified, Pure Storage, and Cylance. These attacks were claimed by an extortion group known as ShinyHunters.
These attacks were conducted using compromised Snowflake credentials stolen by infostealers, which were then used to download company data for use in extortion schemes.
Ticketmaster was among the most widely extorted victims in the Snowflake attack, which led to the theft of personal and ticketing information. After the data was offered for sale online, the company confirmed the breach at the end of May and began notifying affected customers.
Following the initial leak, the threat actors ramped up their extortion attempts by releasing what they claimed were print-at-home tickets and even alleged Taylor Swift tickets in a series of posts on a hacking forum.
While Arkana did not specify the origin of the data, the use of Snowflake references and the file names matching previously leaked files indicates that the group was attempting to resell old stolen data.
Whether or not Arkana previously purchased this data, whether the group is made up of threat actors who previously had the data, or whether they are working with ShinyHunters to sell it is unclear.
On June 9, the entry for the Ticketmaster data had been removed from the Arkana Security data leak site.
The name "ShinyHunters" has been linked to a large number of breaches over the years, including the massive PowerSchool data breach where data was stolen for 62.4 million students and 9.5 million teachers for 6,505 school districts across the U.S., Canada, and other countries.
More recently, Mandiant tied ShinyHunters to a recent campaign targeting Salesforce accounts, where threat actors were breaching accounts to steal customer data and extort companies.
As numerous threat actors tied to ShinyHunters have been arrested over the past three years [1, 2, 3], it is unclear if this is the original group or other threat actors claiming to be them to throw off law enforcement.
BleepingComputer contacted Arkana and Ticketmaster regarding the listing but did not receive a response.
Over 70 Organizations Across Multiple Sectors Targeted by China-Linked Cyber Espionage Group
Over 84,000 Roundcube instances vulnerable to actively exploited flaw
Free online web security scanner






