Trojanized RVTools push Bumblebee malware in SEO poisoning campaign

Update 5/20/25 4:40 PM EST: In response to our questions about the attack, Dell states that the malicious RVTools installer was not distributed from its sites but rather from fake typo-squatted domains.
The company also states that the Dell-managed sites, Robware.net and RVTools.com, were taken offline as they are being targeted in DDoS attacks.
"Dell Technologies operates two websites to distribute our RVTools software: Robware.net and RVTools.com. We are aware of reports alleging that malicious versions of the RVTools software were available on these websites. Our investigation has not identified any indications to suggest a compromise of these websites or the software available for download there."
"We have identified fake websites designed to mimic our websites that may be distributing malware. Our legitimate websites - Robware.net and RVTools.com - have been the subject of recent denial of service (DOS) attacks. As a precaution, we temporarily disabled these sites."
"For the RVTools software, the only Dell-managed sites are Robware.net and RVTools.com. Customers should not search for or download purported RVTools software from any other websites or sources."
This contradicts what ZeroDay Labs researcher Aidan Leon's posted numerous times to Reddit, stating that the files were downloaded directly from the RVTools website.
"I’ve been getting some mixed answers on when it was officially compromised. I’ve been reading different articles stating this isn’t the first time it’s happened," Leon posted to Reddit under the alias TrippyyMuffin.
"Most of the time it’s just unlucky people not noticing SEO poisoning, but this time the actual website was compromised. I noticed it firsthand on Monday (5/12). Tuesday afternoon the website went down, came back online and the malicious file was replaced with a safe one."
"As of now, the website is offline again, so something’s definitely going on behind the scenes. Hopefully it’s in RVTools favor, and not the other way around."
BleepingComputer contacted Leon with follow up questions after receiving the statement from Dell but has not received a response.
While Dell says the malware-laced installers did not come from them, the fact remains that threat actors are distributing Bumblee malware loaders disguised as RVTools.
If you recently installed the software, it is strongly suggested you scan it at VirusTotal to confirm you did not download the malicious version.
Our original unedited story is below.
The official website for the RVTools VMware management tool was taken offline in what appears to be a supply chain attack that distributed a trojanized installer to drop the Bumblebee malware loader on users' machines.
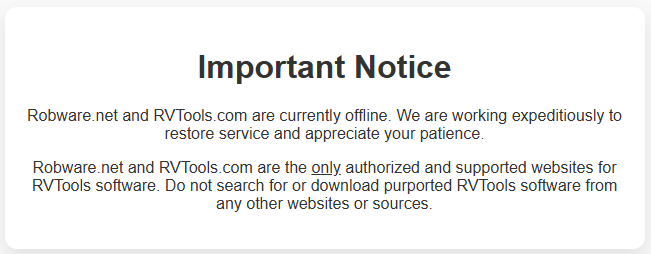
At the time of writing, the official RVTools websites at 'rvtools.com' and 'robware.net' are now displaying a notice warning about the risks of downloading the tool from other sources. The message gives no estimate as to when the download portals will return online.
"Robware.net and RVTools.com are currently offline. We are working expeditiously to restore service and appreciate your patience," reads the website notice.
"Robware.net and RVTools.com are the only authorized and supported websites for RVTools software. Do not search for or download purported RVTools software from any other websites or sources."
RVTool supply chain attack
RVTools, initially developed by Robware and now owned by Dell, is a Windows utility that provides comprehensive inventory and health reporting for VMware vSphere environments.
RVTools is widely regarded as an essential tool for VMware administrators, and VMware's own Virtual Blocks Blog has recognized it as a top utility for vSphere management.
The supply chain attack was first discovered by ZeroDay Labs researcher Aidan Leon, who warned that the official RVTools installer [VirusTotal] attempted to execute a malicious version.dll [VirusTotal] that was detected as the Bumblebee malware loader.
"Further investigation revealed a mismatch between the file hash listed on the RVTools website and the actual file being downloaded," explains Leon.
"The downloaded version was significantly larger and contained the malicious version.dll. Older versions of RVTools did not contain this file and matched their published hashes correctly."
"Approximately one hour after our VirusTotal submission, the number of public submissions rose from 4 to 16. Around this same time, the RVTools website went temporarily offline. When it came back online, the download had changed: the file size was smaller, and the hash now matched the clean version listed on the site"
Bumblebee is a malware loader that is typically promoted via SEO poisoning, malvertising, and phishing attacks. When installed, the malware downloads and executes additional payloads on infected devices, such as Cobalt Strike beacons, information stealers, and ransomware.
The malware has been tied to the Conti ransomware operation, who used the malware to gain initial access to corporate networks. While the Conti ransomware operation shut down in 2022, many of its members split off into other ransomware operations, including Black Basta, Royal, Silent Ransom, and others, who likely still have access to the tooling.
Cybersecurity firm Arctic Wolf also reports seeing trojanized RVTools installers distributed through malicious typosquatted domains, likely promoted through SEO poisoning or malvertising.
"Arctic Wolf has recently observed the distribution of a trojanized RVTools installer via a malicious typosquatted domain," reads the Arctic Wolf report.
"The domain matches the legitimate domain, however, the Top Level Domain (TLD) is changed from .com to .org. RVTools is a widely used VMware utility for inventory and configuration reporting, developed by Robware."
Recently, there have been other reports of SEO poisoning and malvertising campaigns targeting the RVTools brand to trick people into downloading malicious, trojanized installers.
If you downloaded software from these domains, there is a good chance your device is infected with the Bumblebee malware and possibly additional payloads.
As the malware is used by threat actors to gain a foothold on corporate networks, if detected, it is crucial to perform a full investigation to determine if other devices were compromised.
Do not download and execute RVTools installers from unofficial sources claiming to offer a safe/clean version, unless you verify its hash.
European Union sanctions Stark Industries for enabling cyberattacks
PureRAT Malware Spikes 4x in 2025, Deploying PureLogs to Target Russian Firms
Free online web security scanner